Have you ever wondered what an IP address is and why someone would want to know yours?
We explore the legality of obtaining someone’s IP address and different methods to find it. We’ll also discuss the possibility of getting someone’s IP address without their knowledge and the potential risks associated with it.
Find out tips on how to protect your IP address from being compromised and learn more about this crucial aspect of online privacy and security.
What is an IP Address?
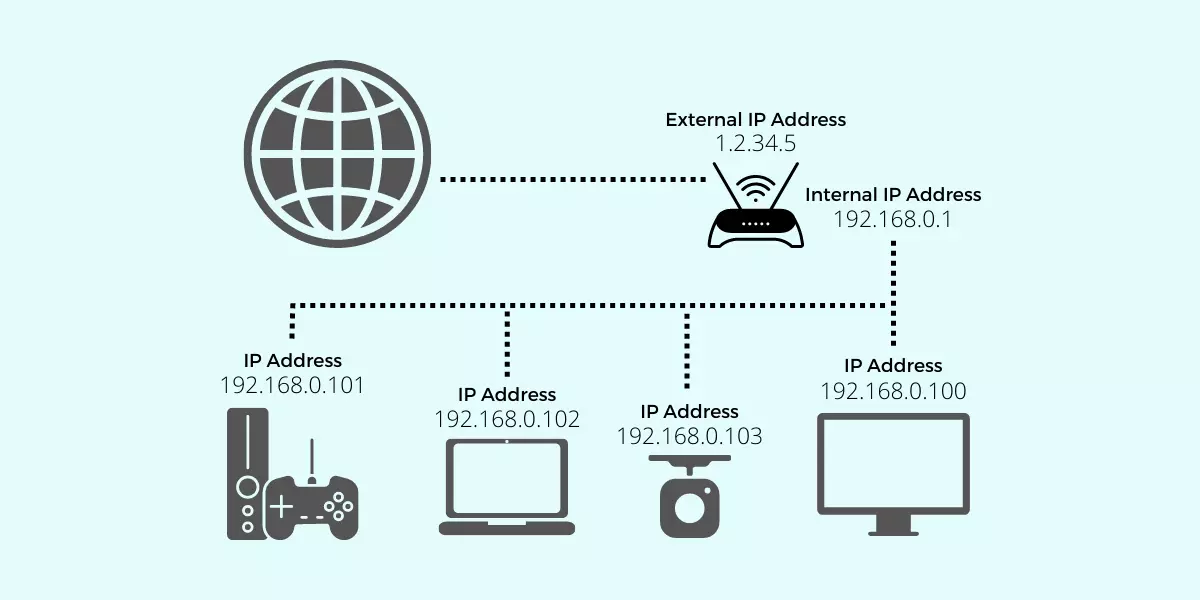
An IP address is a unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication.
These addresses play a crucial role in the functioning of the internet as they serve as identifiers for devices connected to networks. When data is transmitted over the internet, each packet contains the sender’s and recipient’s IP addresses, allowing routers to direct traffic to the correct destination.

The Internet Protocol (IP) governs the entire process of data transmission by providing a set of rules for how data should be packaged, addressed, and sent across networks. It ensures that data gets routed efficiently from source to destination, promoting smooth and seamless communication between various devices and networks.
Why Would Someone Want to Know Someone’s IP Address?
Knowing someone’s IP address can provide valuable information for hackers aiming to track online activities, establish a digital footprint, or potentially launch cyber attacks.
Having access to an individual’s IP address enables hackers to gather data on browsing habits, location, and device information. This can lead to privacy invasion, identity theft, or exposure to malware and phishing attempts. Protecting one’s IP address is crucial to safeguard personal information and prevent potential cyber threats. By concealing IP addresses through virtual private networks (VPNs) or using secure browsing practices, individuals can mitigate the risks associated with unauthorized access and ensure a safer online experience.
Is it Legal to Obtain Someone’s IP Address?
The legality of obtaining someone’s IP address depends on the context and intent, with privacy and cybersecurity concerns playing a crucial role in determining the permissibility of such actions.
Privacy laws often restrict the collection and use of individuals’ digital information, including IP addresses, to protect sensitive data and prevent unauthorized access to personal details. Cybersecurity regulations are in place to safeguard networks from potential threats, emphasizing the importance of secure handling of IP addresses.
Ethical considerations come into play when accessing another person’s digital identifier, as it raises questions about consent, transparency, and respect for individuals’ privacy rights. Proper protocols and consent mechanisms should be followed to ensure that the acquisition of IP addresses is done in an ethical and lawful manner.
How to Find Someone’s IP Address?
Finding someone’s IP address can be achieved through various methods, including utilizing IP lookup tools that provide geolocation data and insights into online activities.
Some commonly used IP lookup tools include websites and software applications that allow users to input an IP address and receive details such as the geographical location, internet service provider, and network type associated with that address.
Hackers may employ more sophisticated techniques, such as phishing emails or malware, to obtain someone’s IP address without their knowledge. By tricking individuals into revealing their IP address, hackers can gain access to sensitive information and compromise their online security.
Geolocating an IP address can have significant implications for tracking purposes, as it enables entities to pinpoint a user’s physical location and monitor their online activities. This information can be used for various purposes, ranging from targeted advertising to law enforcement investigations.
Using a Website or App
One way to find someone’s IP address is by using a website or application that offers IP lookup services, such as email header analysis tools that reveal sender IP information.
These tools function by examining the metadata embedded in emails, which can include valuable details like the originating IP address, timestamp, and various other routing information. By utilizing these intricate digital breadcrumbs, users can trace the path of emails back to their source, potentially shedding light on the sender’s location and online activity.
IP lookup services extend beyond email analysis, enabling individuals and organizations to identify the geographical location, internet service provider, and other relevant data associated with a given IP address.
Using the Command Prompt
Another method to find someone’s IP address involves utilizing the Command Prompt or equivalent tools in the Linux Terminal, utilizing commands like nslookup to query domain-related information.
When utilizing the nslookup command, one can retrieve details about a specific domain name, such as the corresponding IP address and other related DNS information. This tool is incredibly useful for network diagnostics and troubleshooting, as it allows users to identify potential connectivity issues or misconfigurations with domain resolution.
By running an nslookup query, a user can uncover valuable insights into the underlying infrastructure of a website or network, helping them better understand the mapping between domain names and IP addresses. This capability is essential for system administrators and IT professionals who need to ensure the smooth operation of their networks and services.
Using a Network Scanner
Employing a network scanner allows individuals to scan for devices on a network and obtain their IP addresses, leveraging tools like Ping and the Netstat command for network analysis.
Using a network scanner involves initiating a scan to detect all devices connected within a network. The tool sends out requests to devices, prompting responses that reveal their unique IP addresses. This process helps in identifying the network structure and pinpointing the locations of devices within the system.
- Netstat command is particularly useful in displaying active connections and open ports, providing insights into how devices are communicating and which services they are accessing.
- The Ping tool can be used to test connectivity between devices, verifying if they are reachable and responsive.
Is it Possible to Get Someone’s IP Address without Them Knowing?
Obtaining someone’s IP address without their knowledge is feasible through techniques like proxy servers that mask the origin of data packets, potentially bypassing direct identification.
Proxy servers act as intermediaries between a user and the internet, creating a shield that hides the actual IP address, thus enabling online activities to be carried out anonymously. By rerouting the data packets through different servers, these proxies obscure the digital footprint, making it challenging to trace the user’s true location or identity.
While this anonymity safeguard offers internet users a sense of privacy and security, it also raises concerns about potential misuse, as individuals can engage in activities without accountability. The process of packet transmission via proxies can sometimes lead to data leaks or breaches, compromising sensitive information.
What Can Someone Do with Your IP Address?
Possessing your IP address enables individuals to track your physical location, access personal information, or launch disruptive activities like Distributed Denial of Service (DDoS) attacks.
When someone gains access to your IP address, they can easily monitor your online behavior and potentially compromise your privacy. This opens the door to unwanted tracking of your browsing habits and location, putting your security at risk. Additionally, data privacy concerns arise as your sensitive information could be exposed, leading to identity theft or unauthorized access to personal accounts.
The threat of DDoS attacks looms large. Malicious individuals can flood your network with overwhelming traffic, causing it to crash and disrupting your online activities. This not only impacts your network stability but also jeopardizes your overall online security.
Track Your Location
Tracking your location via your IP address involves geolocation services that map your approximate physical whereabouts, posing privacy risks when misused by hackers or malicious actors.
Geolocation services use databases of IP address ranges linked to physical locations to estimate where a device is located. By analyzing network traffic, these services can pinpoint a user’s city or region with remarkable accuracy.
Hackers can exploit this information for malicious purposes such as geo-targeted attacks. They might launch phishing campaigns, distribute malware, or conduct surveillance by tracking a user’s movements in real-time.
Access Your Personal Information
Accessing personal information through an IP address allows unauthorized individuals, including hackers and creators of malicious software, to potentially compromise sensitive data and breach privacy boundaries.
When your IP address is exposed, it can serve as a gateway for cybercriminals to infiltrate your digital world. These bad actors can exploit this digital identifier to launch sophisticated data breaches, gaining access to your personal documents, financial details, and other confidential information, putting you at risk of identity theft. Through your IP address, malicious parties can inject your devices with malware, corrupting your system and possibly rendering it vulnerable to further intrusions.
Launch a Cyber Attack
Using your IP address as a target, malicious actors can launch damaging cyber attacks such as Distributed Denial of Service (DDoS) attacks, compromising network security and disrupting online services.
DDoS attacks, in particular, flood a network with an overwhelming amount of traffic, rendering it inaccessible to legitimate users. This can result in significant financial losses, reputational damage, and downtime for organizations. Security vulnerabilities within systems can be exploited through IP addresses, allowing hackers to infiltrate sensitive data or install malware.
It is crucial to safeguard against these threats by implementing robust cybersecurity measures, such as firewalls, intrusion detection systems, and regular security audits. Education and awareness among users about the risks of malicious online activities are also essential in preventing cyber attacks targeting IP addresses.
How to Protect Your IP Address?
Securing your IP address involves utilizing protective measures like Virtual Private Networks (VPNs) that encrypt data transmissions, enhancing privacy and mitigating risks of exposure.
VPNs play a crucial role in safeguarding your online activities by creating a secure connection between your device and the internet. By channeling your internet traffic through encrypted tunnels, VPNs effectively mask your true IP address, making it difficult for malicious actors to track your online movements.
Encryption protocols employed by VPNs ensure that sensitive data remains secure during transit, protecting your digital identity from potential cyber threats. Leveraging advanced encryption technologies not only bolsters network security but also fortifies your privacy online, crucial in today’s interconnected digital landscape.
Use a Virtual Private Network (VPN)
Employing a Virtual Private Network (VPN) like IPVanish can cloak your IP address, anonymize online activities, and enhance data security through encrypted connections.
By concealing your real IP address, a VPN such as IPVanish safeguards your online identity and shields your browsing history from prying eyes, ensuring utmost privacy.
The secure tunneling protocols used by IPVanish guarantee that your data remains confidential during transmission, preventing cyber-attacks and potential information breaches.
This heightened level of anonymity offered by services like IPVanish enables users to surf the web without the fear of surveillance or tracking, granting them freedom and peace of mind in their online interactions.
Use a Proxy Server
Utilizing a proxy server acts as an intermediary for internet traffic, concealing your IP address and enabling encrypted peer-to-peer communications that enhance online privacy and security.
By rerouting your connection through a proxy server, your actual IP address remains hidden from websites and potential cyber threats.
This added layer of anonymity contributes to a safer browsing experience, especially when accessing public Wi-Fi networks.
Moreover, proxy servers can also bypass content restrictions imposed by certain websites or geographical locations.
Be Wary of Suspicious Links and Emails
Exercise caution when encountering suspicious links or emails that could potentially lead to IP address exposure, phishing attempts, or malware installations, compromising online security.
It is crucial to stay vigilant and be mindful of the various ways cybercriminals can exploit vulnerabilities in online activities. Clicking on seemingly harmless links or opening attachments from unknown sources can result in a breach of sensitive information and unauthorized access to your devices.
By being cautious and skeptical of unsolicited emails or messages, individuals can prevent falling victim to phishing scams that aim to steal personal data or login credentials.
Malware installations through deceptive links can lead to severe repercussions such as data loss, financial theft, or even identity fraud.
Conclusion
Understanding the significance of protecting your IP address is crucial in maintaining online privacy, enhancing security measures, and safeguarding against potential threats posed by hackers and cybercriminals.
When you safeguard your IP address, it serves as a shield, preventing unauthorized parties from tracking your online activities and personal information. By hiding your true IP address, you create a barrier that enhances your anonymity, making it harder for cyber threats to exploit vulnerabilities in your network.
When you prioritize IP address protection, you contribute to the broader efforts of maintaining a secure digital environment. Awareness serves as a potent weapon against cyber risks, enableing individuals to take proactive steps in fortifying their online defenses and minimizing the chances of falling victim to malicious activities.
Frequently Asked Questions
How to get someones ip address?
What is an IP address and why would I need to obtain someone else’s?
An IP address is a unique numerical label assigned to each device connected to a network. You may need to obtain someone else’s IP address for various reasons, such as tracking online activity or troubleshooting connection issues.
Can I get someone’s IP address just by knowing their name or email?
No, you cannot obtain someone’s IP address just by knowing their name or email. You would need additional information, such as their device’s unique identifier or their location, in order to accurately determine their IP address.
Is there a legal way to obtain someone’s IP address?
Yes, there are legal ways to obtain someone’s IP address, such as through a court order or with their consent. It is important to respect people’s privacy and only obtain their IP address for legitimate purposes.
How can I find someone’s IP address through a website?
Many websites have tracking tools that can display a visitor’s IP address. These tools can be found through a simple internet search and may require the person’s consent to track their IP address.
Is it possible to hide or mask my IP address?
Yes, there are ways to hide or mask your IP address, such as using a virtual private network (VPN) or using the Tor browser. These methods can help protect your privacy and prevent others from obtaining your IP address.
What should I do if someone is trying to obtain my IP address without my consent?
If you believe someone is trying to obtain your IP address without your consent, you should take steps to protect your online privacy. This could include changing your device’s settings, using a VPN, or reporting the incident to the proper authorities.